A simple way to track 3rd party risk in your web apps
Driftbot is a free toolkit that runs inside GitHub Actions to monitor your web apps for unexpected third-party scripts and suspicious or malicious code.

What is software supply chain risk?
Most web apps are built with and depend on numerous third-party libraries and frameworks. What happens if one of those packages gets compromised? Would you know?
-
Skimmers
- Consumer credit card numbers remain a lucrative target for hackers. Magecart style malware aims to silently steal credit card details from consumers during the checkout process on popular online commerce sites.
-
Crypto miners
- Since many crypto currency transactions are difficult to trace back to bad actors, hackers often try to hijack the browsers of unsuspecting users and utilize their processing power to mine crypto currencies.
-
Credential harvesting
- Even sites that don't handle commerce transactions can be targeted if hackers are after login credentials for that site. The credentials are then silently exfiltrated to systems owned by the hackers - often via background XHR or WebSocket requests.
-
Malware
- Hackers may try to exploit your users' systems directly either through browser vulnerabilities or by tricking users into downloading or installing malicious software. The system can then be forced to join a botnet for further malicious purposes.
-
Malicious adware
- Hackers may try to exploit lax review policies at ad networks and inject malicious code into ads that appear to function normally. It isn't until the ads go live on the ad network that users are then targeted with the attacker's malicious code.
Use your existing GitHub account
Driftbot uses a headless Chrome browser to visit your site simulating a real user. You can monitor a single page, or record and replay a complex series of user flows and interactions to further mimic real user behaviors on your site. Driftbot runs as a GitHub Action in any public or private repo.
When the bot detects an unknown host, it will create an issue alerting you to the detection. You can then review the details to determine if that host should be considered approved. A full log of third-party connections is recorded in the GitHub Action run logs for future inspection.
You can run the bot on a schedule or trigger it manually, just like any other GitHub Action.
-
Commented 1d ago
Unauthorized script hosts detected:
xn--80ak6aa92e.com
g1thubassets.com
evilcdn.com
-
GitHub
-
-
Commented 2h ago
No unauthorized hosts detected.
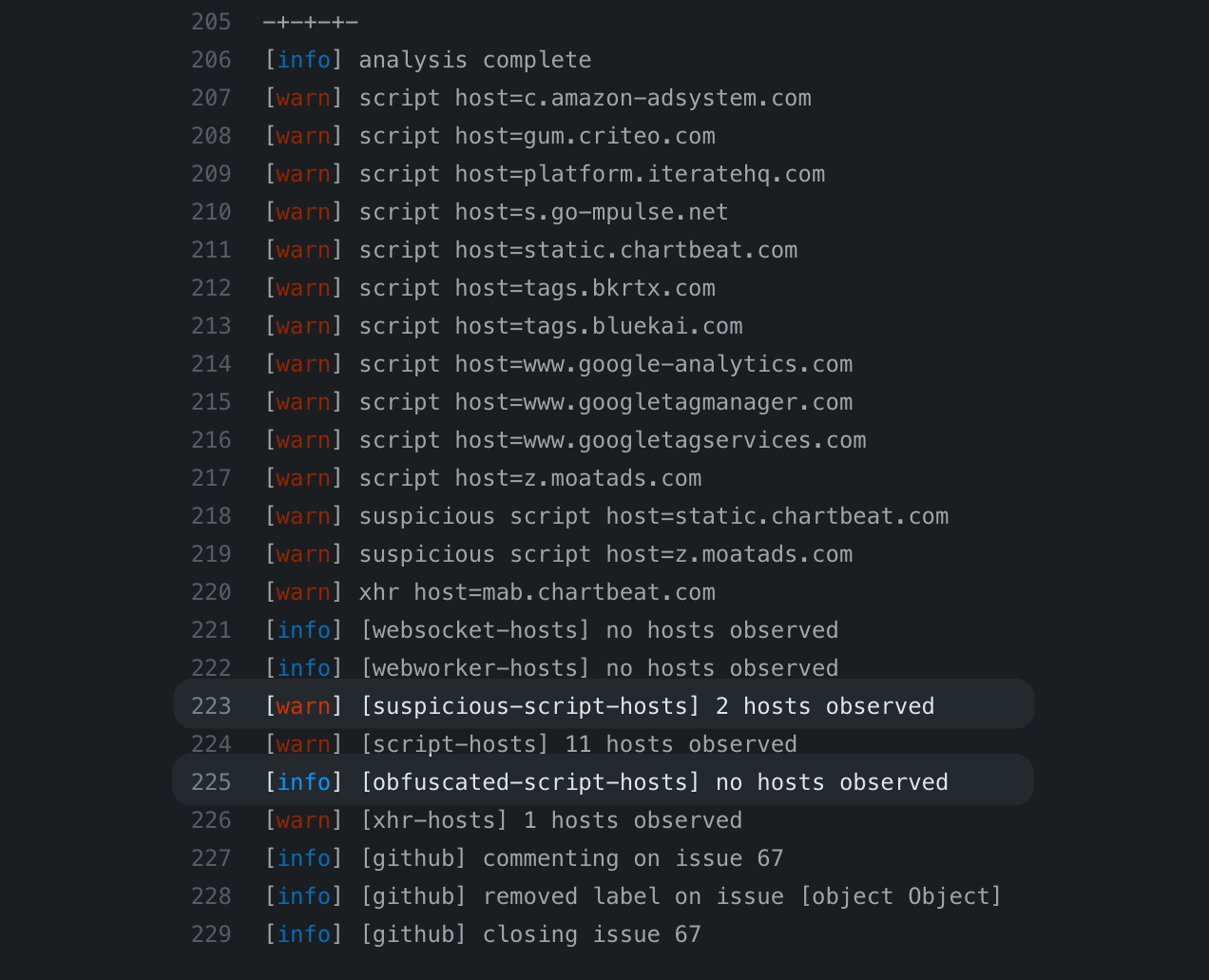
Automated code analysis
In addition to simply alerting on unexpected script sources, Driftbot also analyzes the JavaScript code on your site, even if it isn't triggered to run.
The bot will detect heavily obfuscated JavaScript code. Obfuscated code is not malicious by itself, but hackers and aggressive ad networks will often use obfuscation to try to hide their intentions in confusing code.
The bot will also detect suspicious JavaScript function calls, even if they don't execute. Driftbot uses Esprima to generate an Abstract Syntax Tree (AST) of the JavaScript on your site to detect when calls like eval, atob, and btoa are called.

Get started in under 5 minutes
Driftbot runs in your own GitHub account and uses GitHub Actions to drive a headless Chrome browser that interacts with your site.
Install your own bot